Shield Your Business: Best IT Vendor Risk Management Solutions Compared
April 8, 2025

Discover how healthcare it service management boosts patient care, efficiency, and compliance in modern healthcare systems.
April 18, 2025

Discover top hardware backup solutions to secure your data, ensure business continuity, and protect against cyber threats.
April 15, 2025

Discover how Cloud migration consulting services optimize your business with expert strategies for seamless cloud transitions.
April 15, 2025
April 8, 2025
IT vendor risk management solutions are crucial for any business looking to safeguard its operations from cybersecurity threats and data breaches. Here's a quick summary of what these solutions typically offer:
In an age where cyber threats are a constant menace, managing your vendor risks effectively isn’t just a strategy—it’s a necessity. According to the 2023 Cost of a Data Breach report by IBM and the Ponemon Institute, the average cost of a data breach has reached USD 4.45 million, with compromised vendors amplifying the damage. This highlights how vendor vulnerabilities can quickly become your vulnerabilities.
As businesses grapple with increasing security challenges, adopting comprehensive IT vendor risk management solutions offers assurance that you're not just prepared—but actively protecting your enterprise.
I'm Steve Payerle, President of Next Level Technologies, where I've been leading efforts to transform how businesses manage their IT needs. With years of experience delivering solutions that prioritize efficiency and security, I've seen how IT vendor risk management solutions can fortify businesses, reduce disruptions, and ensure compliance across the board.
In the field of protecting your business from cyber threats, IT Vendor Risk Management Solutions play a pivotal role. Let's break down how these solutions work through the lens of the risk management lifecycle, vendor identification, and risk mitigation.
The risk management lifecycle is a continuous process that ensures your business remains secure. It starts with vendor identification and extends through assessment, monitoring, and remediation.
Vendor Identification: This initial step involves recognizing all third-party vendors your business interacts with. Knowing who your vendors are is crucial because, as noted in the Verizon 2022 Data Breach Investigations Report, 62% of data breaches involve third-party vendors.
Risk Assessment and Monitoring: Once identified, vendors undergo a thorough risk assessment. This includes evaluating their security postures and identifying potential vulnerabilities. Solutions like Bitsight offer insights into over 25 key risk vectors, providing a comprehensive view of potential threats.
Risk Remediation: The final stage involves addressing identified risks. Automated workflows ensure that vulnerabilities are swiftly mitigated. UpGuard, for instance, provides in-built risk remediation workflows to prioritize and address risks effectively.
Identifying and cataloging all your vendors is the foundation of any successful risk management strategy. This step ensures you have a clear picture of who might have access to your data and systems. Without this knowledge, you're essentially blind to potential threats.
Risk mitigation is about reducing the potential impact of identified risks. This involves:
Implementing Controls: Once risks are identified, controls are put in place to mitigate them. This could involve updating security protocols or requiring vendors to adhere to specific security standards.
Continuous Monitoring: Real-time monitoring tools keep an eye on vendor activities, ensuring any changes in their security posture are detected immediately. This is crucial for maintaining a secure environment.
Collaboration and Communication: Effective risk mitigation requires open lines of communication with vendors. Tools that facilitate collaboration can help ensure that both parties are aligned on security expectations and remediation efforts.
By understanding and implementing these components of IT Vendor Risk Management Solutions, businesses can better protect themselves from the costly repercussions of data breaches. As cyber threats continue to evolve, having a robust risk management strategy is not just beneficial—it's essential.
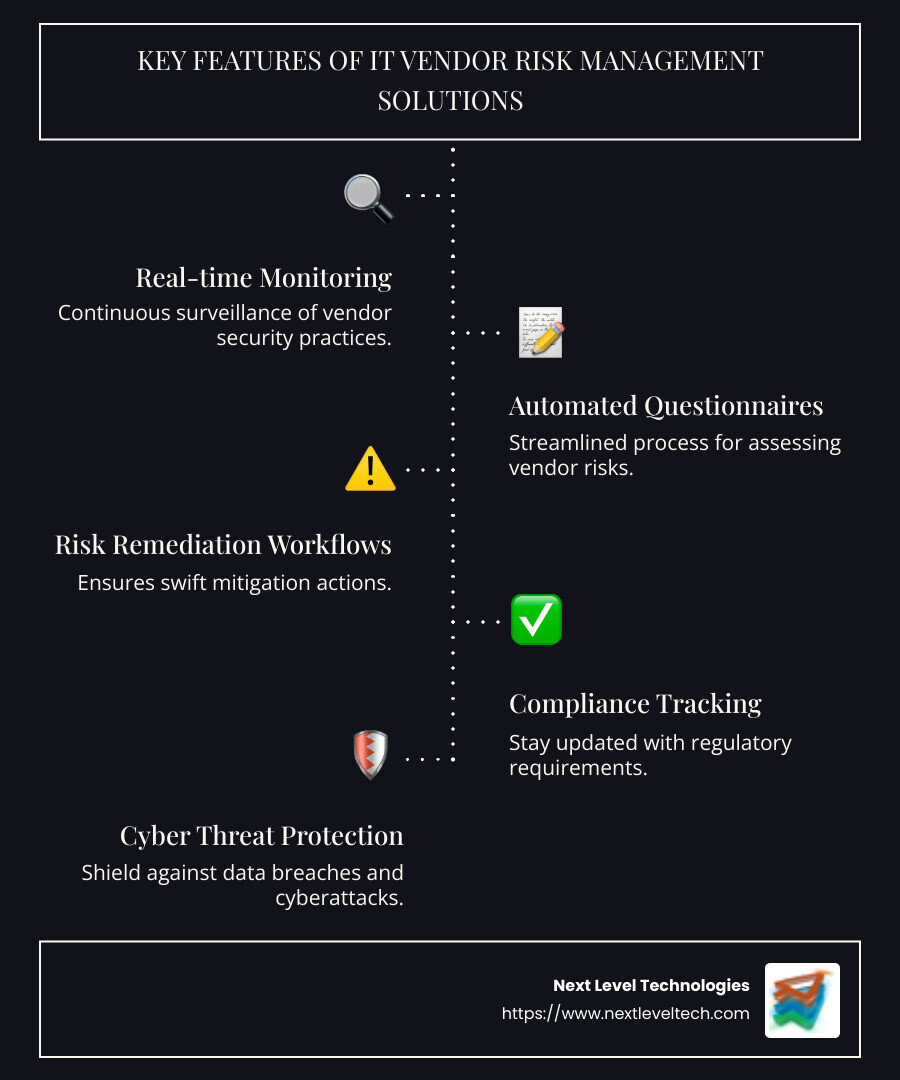
When it comes to safeguarding your business, IT Vendor Risk Management Solutions are indispensable. Let's explore their key features: risk assessment, threat monitoring, and automation.
Risk assessment is the backbone of any vendor risk management strategy. It involves evaluating the security measures and vulnerabilities of your vendors. Vendor Risk Assessment Management tools streamline this process by providing a comprehensive view of risks at every stage of the vendor lifecycle.
Imagine having a tool that not only helps you conduct due diligence but also continuously monitors your vendors. That's what you get with a robust risk assessment feature. It ensures that your vendors meet your security standards and helps you identify potential threats before they become serious issues.
With cyber threats evolving constantly, real-time threat monitoring is crucial. This feature allows businesses to keep a vigilant eye on their vendors' security postures. Attack Surface Monitoring is a key component, providing insights into vulnerabilities that could be exploited by cybercriminals.
For instance, Prevalent's Global Vendor Intelligence Network offers comprehensive monitoring, even tracking dark web forums to detect potential threats. This kind of proactive monitoring helps businesses stay ahead of potential breaches and protect their data.
Automation is the game-changer in vendor risk management. It streamlines processes, reduces manual errors, and improves efficiency. Security Questionnaire Automation is a perfect example. By automating the distribution and tracking of security questionnaires, businesses can ensure timely completion and minimize disruptions.
Additionally, Risk Remediation Workflows automate the process of addressing identified risks. This means that once a vulnerability is detected, the system can automatically trigger corrective actions, ensuring swift remediation.
By integrating these features, IT Vendor Risk Management Solutions empower businesses to manage vendor risks effectively. They provide a comprehensive approach to identifying, assessing, and mitigating risks, ensuring your business remains secure in an increasingly complex digital landscape.
In the next section, we'll dig into the benefits of automated IT Vendor Risk Management, highlighting how it improves velocity, scalability, and collaboration.
In today's digital world, automated IT Vendor Risk Management solutions are a game-changer. Let's explore how they improve velocity, scalability, and collaboration.
Traditional vendor risk assessments can be slow and cumbersome. They often take weeks or even months to complete. This slow pace can leave your business vulnerable to new threats that emerge during the assessment process.
With automation, the speed of risk assessments skyrockets. Automated solutions provide quicker assessments, allowing businesses to gain a comprehensive view of a vendor's security posture in a fraction of the time. This rapid turnaround is crucial when managing hundreds or even thousands of vendors. Automated tools like MetricStream can instantly notify security teams of new threats before vendors have even addressed them.

As businesses grow, so does their network of vendors. Managing this expanding ecosystem manually is nearly impossible. Automated IT Vendor Risk Management solutions offer simple scalability, enabling businesses to handle a growing number of vendors without adding extra resources.
These solutions streamline cybersecurity assessments and processes, allowing your existing team to manage more with less. This means you can maintain thorough risk assessments and due diligence, even as your vendor base expands.
Working with vendors to mitigate cybersecurity risks can be challenging. Communication gaps and misunderstandings can slow down the risk management process. Automated solutions foster easier collaboration by providing a common platform where businesses and vendors can review the same data. This shared view offers clarity around security issues and helps in making informed cyber threat intelligence decisions.
For example, solutions like ProcessUnity offer a shared platform that enables both parties to work together seamlessly, ensuring that security measures are understood and implemented effectively. This improved collaboration leads to faster resolution of security issues and a stronger, more secure vendor ecosystem.
By leveraging these benefits, businesses can ensure their IT vendor risk management is not only effective but also efficient and adaptable to the ever-changing threat landscape.
Next, we'll explore how to build an effective vendor risk management program, focusing on documentation, vendor selection, and due diligence.
Creating a solid Vendor Risk Management Program is essential in today's interconnected business world. Let's break down the key steps: documentation, vendor selection, and due diligence.
Effective documentation is the backbone of any successful vendor risk management program. It ensures that everyone is on the same page and that processes are repeatable and consistent.
Start by clearly defining your risk management policies and procedures. This includes documenting how you identify, assess, and mitigate vendor risks. Include detailed guidelines on how to handle various scenarios, from onboarding new vendors to managing ongoing relationships.
A structured documentation process helps maintain transparency and accountability. It also serves as a reference point for your team and vendors, ensuring compliance with industry standards and regulations.
Choosing the right vendors is crucial for minimizing risk. Begin by identifying potential vendors that align with your business goals and values. A thorough vetting process should follow.
Evaluate vendors based on their security posture, reputation, and compliance with relevant regulations. Use standardized questionnaires and assessment tools to gather information about their cybersecurity practices.
Consider vendors' past performance and any previous incidents. This historical data can provide valuable insights into their reliability and risk levels.
Due diligence is about digging deeper into a vendor's operations to uncover potential risks. This step goes beyond initial assessments and involves continuous monitoring and evaluation.
Regularly review vendors' security practices, financial health, and compliance status. Automated solutions can streamline this process by providing real-time updates and alerts about any changes in a vendor's risk profile.
Conduct periodic risk assessments and audits to ensure vendors continue to meet your risk management standards. This ongoing vigilance helps catch potential issues before they escalate into serious problems.
By focusing on documentation, vendor selection, and due diligence, your business can build a robust vendor risk management program that safeguards against potential threats.
Next, we'll answer some frequently asked questions about IT vendor risk management solutions, including how to manage vendor risk and build a comprehensive program.
Managing vendor risk is all about understanding the potential threats that vendors might introduce to your business and taking steps to mitigate them. Here's a simple breakdown:
Vendor Identification: Start by identifying all vendors your business interacts with. This includes anyone providing products or services that could impact your IT environment.
Risk Assessment: Once identified, assess the risk each vendor poses. This involves evaluating their security measures, compliance with regulations, and any past security incidents.
Continuous Monitoring: Regularly monitor vendors to ensure they maintain their security posture. Automated tools can help track changes in a vendor's risk profile.
Risk Mitigation: Develop strategies to address identified risks. This might include changing vendor terms, implementing additional security measures, or even discontinuing the relationship if necessary.
An effective IT security risk management strategy revolves around three core principles: confidentiality, integrity, and availability.
Confidentiality: Protect sensitive information from unauthorized access. Ensure that only authorized personnel have access to data, and use encryption to safeguard information.
Integrity: Maintain the accuracy and reliability of data. Implement checks to ensure data is not altered or tampered with during storage or transmission.
Availability: Ensure that information and systems are accessible when needed. This means having robust systems in place to prevent downtime and ensuring quick recovery from disruptions.
Building a successful vendor risk management program involves several key steps:
Vendor Selection: Choose vendors who align with your security standards and business goals. Use a thorough vetting process to evaluate their security posture and compliance with regulations.
Due Diligence: Conduct in-depth investigations into potential vendors. This includes reviewing their financial health, security practices, and compliance status.
Documentation: Maintain comprehensive records of all vendor interactions and assessments. This ensures transparency and accountability in managing vendor relationships.
Ongoing Assessment: Continuously assess and monitor vendors to ensure they meet your risk management standards. Regular audits and automated monitoring tools can help keep track of changes in a vendor's risk profile.
By focusing on these areas, businesses can effectively manage vendor risks and improve their overall security posture.
In the next section, we'll dig into more detailed strategies and tools that can help improve your vendor risk management efforts.
In today's interconnected digital landscape, managing vendor risks is not just a necessity—it's a strategic advantage. At Next Level Technologies, we understand the critical role that comprehensive managed IT services play in safeguarding your business against potential threats posed by third-party vendors.
Our approach is simple yet effective. We offer comprehensive solutions that cater to businesses of all sizes, ensuring that you can focus on what you do best while we take care of the complexities of IT vendor risk management. Our services include everything from vendor identification and risk assessment to continuous monitoring and risk mitigation.
Why choose us? Here’s what sets us apart:
Expertise Across Locations: With locations in Charleston, WV, Columbus, OH, and Worthington, OH, we bring local expertise with a global perspective.
Custom IT Solutions: We specialize in industries often overlooked, providing custom solutions that meet your unique needs.
Proactive Risk Management: Our proactive approach ensures that risks are identified and addressed before they become threats, enhancing your business resilience.
Scalable and Flexible: As your business grows, our IT solutions scale with you, ensuring that your vendor risk management remains robust and effective.
By partnering with Next Level Technologies, you're not just getting a service provider—you're gaining a dedicated partner committed to your success.
Explore how our managed IT services can transform your approach to vendor risk management. Let us help you shield your business from potential threats and drive sustainable growth.
In the field of IT vendor risk management, being proactive is key. With the right solutions and strategies, you can turn potential risks into opportunities for growth and innovation.
Discover how healthcare it service management boosts patient care, efficiency, and compliance in modern healthcare systems.
April 18, 2025
Discover top hardware backup solutions to secure your data, ensure business continuity, and protect against cyber threats.
April 15, 2025
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
