Secure Your Digital Life with an Authenticator App
August 19, 2025

Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026

Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026

Find the best Remote IT Support Business for your small business. Learn how to define needs, evaluate providers, and secure your tech.
February 6, 2026
August 19, 2025
An authenticator app is a mobile application that generates time-sensitive, one-time codes to add an extra layer of security when logging into your accounts. Here's what you need to know:
What it does:
How it works:
Popular options:
With around 88%-95% of data breaches still caused by human error and passwords alone no longer considered safe, authenticator apps have become essential for protecting both personal and business accounts. The recent Chrome extension hacks that bypassed 2FA for 2.6 million users show that even advanced security measures need proper implementation and management.
As Steve Payerle, President of Next Level Technologies, I've helped hundreds of businesses in Columbus, Ohio and Charleston, WV implement comprehensive cybersecurity solutions, including authenticator app deployment as part of our managed IT services. Our extensive cybersecurity training has shown us that proper 2FA implementation is one of the most effective ways to prevent unauthorized access to critical business systems.
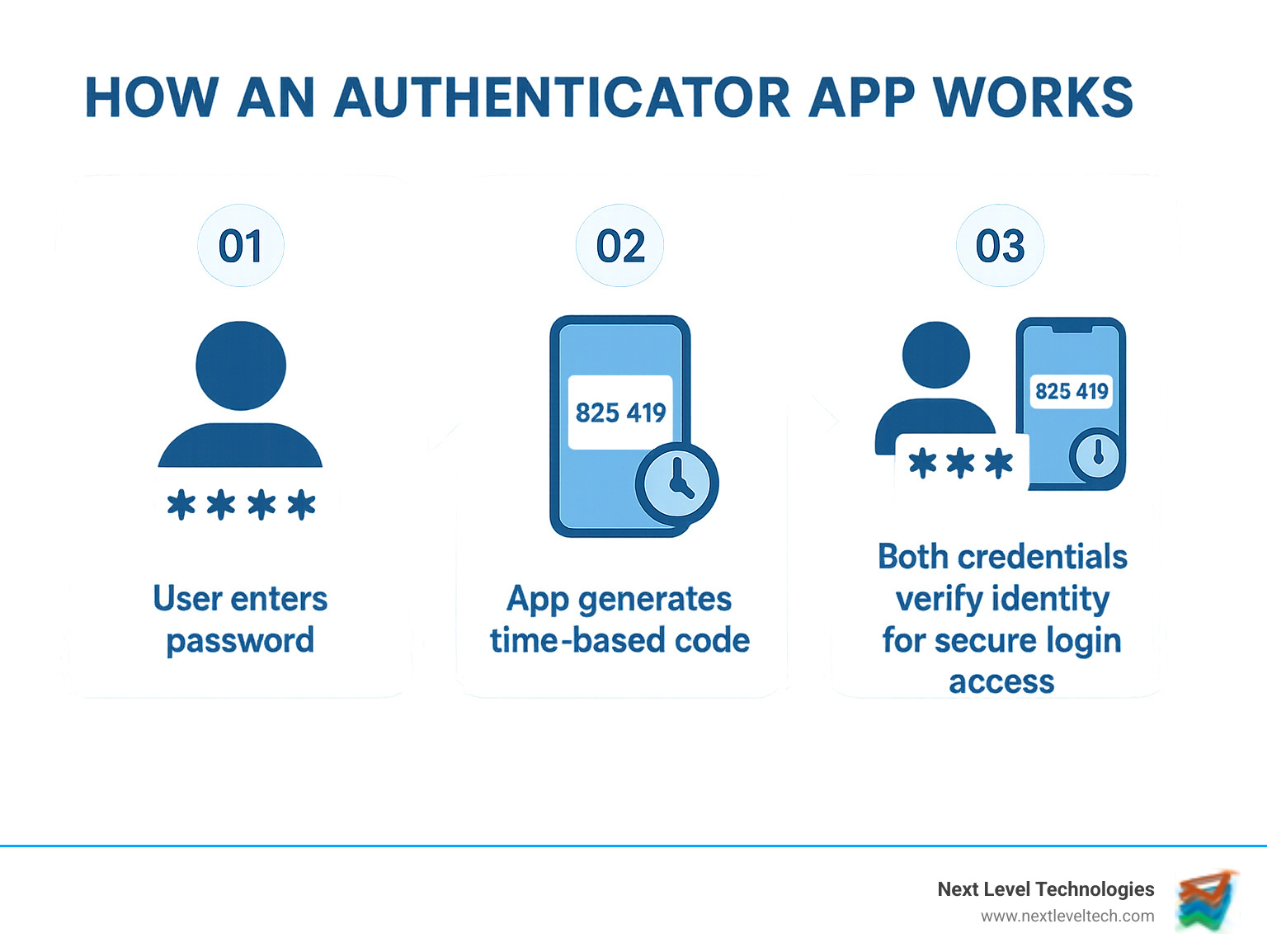
When you log in and enter that 6-digit code from your phone, your authenticator app is performing a complex security check. The magic behind this is a system called Time-based One-Time Passwords (TOTP), which follows the TOTP open standard.
When you first link an account, your authenticator app and the service exchange a shared secret key. Using this key and the current time, both your app and the service's server generate the exact same 6-digit code simultaneously. These codes refresh every 30 seconds.

When you enter the code, the website verifies it matches the one they generated. Because the code is time-sensitive and tied to a secret key only you possess, it's nearly impossible for hackers to guess.
While an alternative method called HMAC-based One-Time Passwords (HOTP) uses a counter instead of time, TOTP is the standard for most services due to its security and simplicity.
A key feature our clients at Next Level Technologies appreciate is that your authenticator app works completely offline after setup. Once the initial QR code scan transfers the secret key to your phone, you don't need an internet or data connection to generate codes. This ensures you have access even during a network outage.
The QR code setup is simple: enable 2FA on a service, scan the displayed QR code with your app, and the account is instantly added. No complex configuration is needed.
Through our extensive cybersecurity training with businesses in Columbus, Ohio and Charleston, WV, we've seen how this technology strengthens Multi-Factor Authentication Solutions. Combining something you know (password) with something you have (your phone) creates a formidable security barrier.
Choosing the right authenticator app involves balancing security with convenience. After helping businesses in Columbus, Ohio and Charleston, WV implement secure authentication, our team at Next Level Technologies has found the best app is the one you'll use consistently. Whether you prioritize maximum protection or seamless cross-device integration, there's an option that fits your needs.
| Feature | Google Authenticator | Microsoft Authenticator | Proton Authenticator | Open-Source Apps |
|---|---|---|---|---|
| Cloud Backup | Yes (via Google Account sync) | Yes | Yes | Varies |
| Cross-Device Sync | Yes (via Google Account sync) | Yes | Yes | Varies |
| Passwordless Options | No | Yes (for Microsoft accounts) | No | No |
| Open-Source | No | No | Yes | Yes |
| PIN/Biometric Lock | Yes | Yes | Yes | Yes |
| Push Notifications | No | Yes | No | No |
| Desktop Client | No | No | Yes | Varies |
When our cybersecurity team evaluates authenticator app options, we focus on non-negotiable features that prevent major issues.
Cloud backup is critical. Losing your phone without a backup can lock you out of your accounts, making recovery a difficult process of support tickets and identity verification. Apps like Microsoft Authenticator have long offered encrypted cloud backup, and Google Authenticator recently added a similar feature.
Cross-device sync is a game-changer for professionals using multiple devices. Having codes automatically sync between your phone and tablet eliminates friction and improves workflow.
App-level security adds another layer of protection. Using a PIN or fingerprint lock means that even if someone accesses your open uped phone, they still can't get to your authentication codes.
End-to-end encryption for backups is a key feature of privacy-focused apps like Proton Authenticator. It ensures your authentication data remains encrypted and unreadable, even when stored in the cloud.
If an app is difficult to use, it won't be used consistently. These convenience features are vital for maintaining strong security habits.
Push notifications simplify logins. Instead of typing codes, apps like Microsoft Authenticator send a login approval request directly to your phone. A single tap completes the login, making the process faster and more secure.
Passwordless sign-in is the future of authentication. Microsoft leads in this area, allowing you to approve logins for their services with a fingerprint or face scan, eliminating the password entirely.
Desktop clients and browser extensions offer convenience, but our extensive cybersecurity training advises caution. While some apps offer legitimate desktop versions, many browser extension authenticators can be risky. The recent Chrome extension hacks that compromised 2.6 million users prove that convenience can come at a high security cost.
At Next Level Technologies, we often implement Adaptive Multi-Factor Authentication for business clients. This approach only requires the second factor during unusual login attempts, balancing security with user convenience.
The choice between open-source and proprietary apps comes down to trust and transparency.
Open-source apps like Proton Authenticator and FreeOTP allow anyone to inspect their code. This community verification makes it harder to hide vulnerabilities or malicious behavior.
Proprietary apps like Google and Microsoft Authenticator offer polished interfaces, dedicated support, and seamless ecosystem integration. While their code isn't public, they are backed by large corporations with a strong incentive to maintain security.
Both approaches can be secure. Corporate backing often means faster updates and professional support, while community verification provides transparency. The right authenticator app is one that matches your technical comfort, fits your routine, and gives you confidence in your account security.
Setting up an authenticator app is a straightforward process. In our experience helping businesses across Columbus, Ohio and Charleston, WV, we've found that anyone can master the setup in minutes, and the peace of mind it provides is immeasurable.
First, download your chosen authenticator app from the App Store or Google Play Store. Most popular options are free.
After opening the app, you'll need to grant camera permissions. This is a safe and necessary step that allows the app to scan QR codes, which is the easiest way to add accounts.
To add an account, go to the security settings of an online service and enable two-factor authentication. They will display a QR code. In your authenticator app, tap "Add account" and point your camera at the code. The app will automatically capture the setup information.
If a service provides a text-based secret key instead of a QR code, select the manual entry option in your app and carefully type or paste the key.
The final step is verification. The service will ask for the current code from your authenticator app to confirm that the link was successful.

These practices, drawn from our extensive cybersecurity training, are essential for long-term security.
Save your recovery codes immediately. When you enable 2FA, services provide backup codes. These are your lifeline if you lose your phone or delete the app. Print and store them securely offline—in a locked drawer or safe—not on a digital device.
Lock down your authenticator app with a PIN or biometric protection. This adds a critical layer of security, preventing access to your codes even if someone gets into your open uped phone.
Enable cloud backup or syncing if your app offers it. Services like Microsoft Authenticator and Google Authenticator make restoring your accounts on a new device seamless.
When transferring to a new phone, plan ahead. Use the cloud backup feature or your app's built-in transfer tool before wiping your old device to avoid getting locked out.
Keep your authenticator app updated. Developers regularly release patches for security vulnerabilities, a simple step that aligns with the habits we outline in our 10 Cybersecurity Tips for Small Businesses.
Modern authenticator apps feature universal compatibility because most services use the same TOTP standard. This means one app can protect your entire digital life.
You can use a single authenticator app for:
This consolidation simplifies security management. At Next Level Technologies, we've seen this transform how clients view 2FA—not as a burden, but as a reliable digital bodyguard protecting what matters most.
While an authenticator app is a powerful security upgrade, it's not invincible. Understanding the potential risks and evolving tactics of bad actors is key to staying protected.
The most common threat is phishing attacks, which trick users into giving up their credentials. An attacker might send a convincing email from your bank, leading you to a fake login page. When you enter your password and the code from your authenticator app, you've handed the attacker both keys to your account.
This highlights a critical fact: around 88%-95% of data breaches are still caused by human error. The recent Chrome extension hacks that affected 2.6 million users often started with phishing emails, reminding us that vigilance is our best defense.
Session hijacking is another method that can bypass your authenticator app. If an attacker steals your active session cookie—a temporary pass that keeps you logged in—they can access your account without needing a password or code. This was a technique used in the Chrome extension attacks.
Browser extension vulnerabilities are a growing concern for our cybersecurity practice in Columbus and Charleston. While some extensions offer 2FA convenience, they can also be attack vectors. Our extensive cybersecurity training has taught us to be cautious with browser-based tools that request broad permissions.
The most direct risk is a lost or stolen device. If your phone is open uped, an attacker could access your authentication codes. This is why device-level security and app-level locks are so important.
This is also where recovery codes become absolutely critical. These backup codes are your lifeline if your phone is lost, broken, or your authenticator app fails. Not storing them properly can lead to being locked out of critical systems.
Managing these risks isn't about avoiding authenticator apps, but about building a multi-layered defense. At Next Level Technologies, our Cybersecurity Services focus on this approach, combining proper authenticator app deployment with employee training and robust recovery procedures to account for both technological and human factors.
Over years of helping businesses in Columbus, Ohio and Charleston, WV, our team has answered countless questions about authenticator apps. Based on our extensive cybersecurity training, these are the most common inquiries.
Yes, absolutely. Most online services use the universal TOTP standard (Time-based One-Time Password), meaning they are compatible with any standard authenticator app. You can use a single app, like Microsoft Authenticator or Google Authenticator, to secure accounts from hundreds of different providers, including social media, banking, email, and business tools. This consolidation is a key benefit, making it much easier to manage your digital security from one central place.
Losing your phone doesn't have to be a disaster if you've prepared. Your primary recovery methods are:
If you have no backups, you must use each service's individual account recovery process. As soon as you realize your phone is missing, use its remote wipe feature (like Apple's Find My or Google's Find My Device) to protect your data.
No. Once an account is added to your authenticator app, it works completely offline. The app uses a stored secret key and your phone's internal clock to generate codes, so you don't need an internet or cellular connection. This makes authenticator apps more reliable than SMS-based 2FA, which requires cell service. You only need an internet connection for the initial setup of a new account.
Authenticator apps are one of the most powerful steps you can take to protect yourself online. In a landscape where around 88%-95% of data breaches stem from human error and sophisticated attacks like the recent Chrome extension hacks are common, this extra security layer is essential.
An authenticator app transforms your smartphone into a personal security guard that works 24/7, even without an internet connection. It generates the codes that protect everything from your social media and online banking to critical business systems. The beauty of modern apps lies in their simplicity and universal compatibility, making it easy to dramatically improve your digital security.
At Next Level Technologies, we've watched countless businesses in Columbus, Ohio, and Charleston, WV transform their security posture with proper 2FA implementation. Our team's extensive cybersecurity training has shown us that taking these foundational steps provides true peace of mind. Cybersecurity isn't about fear—it's about empowerment.
Your digital life is worth protecting. Great security is about building layers of protection, staying informed, and having trusted partners. Ready to strengthen your cybersecurity foundation? Find out how our Managed IT Services and IT Support can help you build a comprehensive security framework that protects what matters most. Let's work together to make your digital world safer.
Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026
Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
